Yesterday the XREX secops team noticed an AML alert — one of our users tried to withdraw funds into wallet: 1BT5vBb9WKudUAX51jiWi3pAawobD3mZwM; our system blocked this withdrawal due to its high CipherTrace risk score.
(Also published on Hacker Noon)

[Investigation Summary]
=======
Victims: 1000+ people from worldwide, scammed into making 2,079 transactions.
Scammed funds: 205.4925067 BTC (roughly $3M at writing time).
Attribution: Nigerian “Operation N-Fiverr.”
Time frame: they’ve been running multiple campaigns starting 2017 Dec.
Tool supplier: outsourced to iPongDev Tech (also Nigerian), in PHP+Laravel.
Websites: they’ve worked with iPongDev.Tech to launch more than 30 different scam websites, by modifying from the same codebase.
Stolen passports and IDs: by asking victims to KYC, we believe they’ve stolen these victim’s IDs to create KYC’ed accounts at exchanges; they use these accounts to collect defrauded funds from victims.
Wallets: a combination of own wallets, as well as compromised, KYC’ed wallets of Remitano, Gemini. We published a list of 48 wallet addresses used by this actor.
Domains and IPs: we published a list of 49 domains and 13 IP addresses used by this actor.
Investigation method: XREX obtained Operation N-Fiverr’s source code and backend admin panel access.
=======
[Investigation]
Having stopped our user’s withdrawal into this actor’s wallet, the XREX secops team started to trace back into their infrastructure. We stumbled upon a directory listing vulnerability within the actor’s infrastructure, which allowed us to obtain the source code of their attack tools:

Investigating into our obtained source code of this actor, we understood they bought their codebase from the Nigerian company iPongDev Tech. iPongDev sold codebases relating to crypto exchange, wallet, and investment. For the basic framework, they mostly used PHP and Laravel, and for k-line and other visualizations they used TradingView and coinlib.io widgets.

From this actor’s backend admin panel, we can see that their entire scam tooling is modified from a crypto investment platform sold by iPongDev Tech:

Using the backend panel, we can see the list of victims and their defrauded amounts and dates:

The profit numbers are of course fake but more importantly, they do not approve withdrawals, which effectively makes this own operations a scam. While they’ve not approved a single withdrawal request, some users have sadly reached out to them via their customer support system hundreds of times. Of course, they’ve never replied.

[Money Flow]
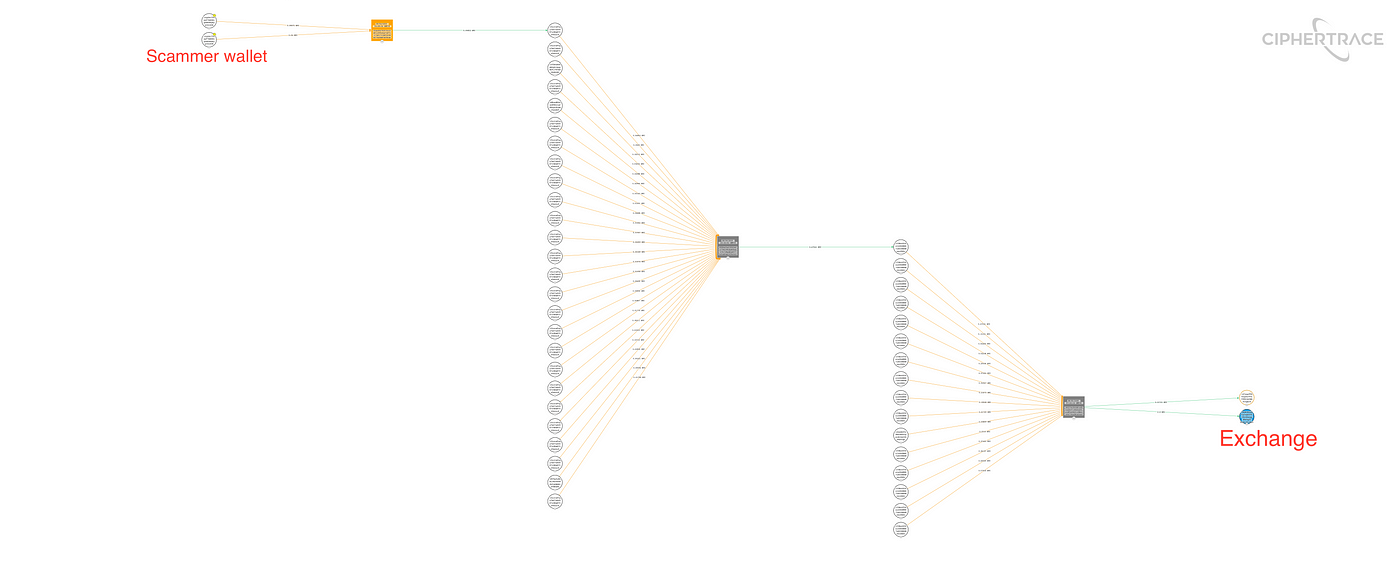
Operation N-Fiverr’s money flow has been consistent — as soon as a victim is defrauded into transferring BTC into one of their wallets, they will immediately forward those BTC into either a) their other on-chain wallets, or b) their exchange wallets.
We’ve also found them to be directly using compromised Remitano and Gemini wallets for victim deposits.
[Attack]
Operation N-Fiverr attracts victims by pitching them various high-interest rate crypto investment platforms. By modifying from the same codebase, they’ve worked with iPongDev.Tech to launch more than 30 different scam websites:







In general, these fraudulent platforms offer:
- $20 USD signup bonus
- Minimum deposit amounts ranging from $1,000 USD to $50,000 USD
- Very high interest rate: 10% in 12 hours, 20% in 24 hours, etc
- Referral features and high referral commissions
- The profits are shown in realtime
Once a victim wants to withdraw funds, Operation N-Fiverr will launch a second wave of attack:
- Asking the victim to further deposit 10%-20% of the earned profits prior to withdrawal, saying that this is “per company policy”
- Asking the victim to first deposit withdrawal fees in order for the withdrawal to be approved
Many victims have been defrauded into sending in more funds. Once a victim finally realizes she may never be getting her funds back, the actor cuts off all communication.
Using the particular wallet address used against our user, we were able to find the following abuse reports of Operation N-Fiverr:


[Collaboration]
We were able to block our user’s withdrawal into Operation N-Fiverr’s wallet due to AML triggers by CipherTrace; we thank them also for their strong technical support during this investigation.

This investigation is by no means complete; we’ve had very limited time but wanted to publish asap so the community can collectively blacklist this actor’s resources and mitigate this attack.
We will appreciate any help from the community; please feel free to reach us at secops@xrex.io.
[Blacklists and Blocklists]
Operation N-Fiverr’s malicious domains:
bitcointradex[.]com
24bitchainmining[.]com
216liveoption[.]com
fxltetrade[.]com
cryptoprofitmaking[.]com
tradeoptionfx[.]com
trade[.]fxltetrade[.]com
trade365forex[.]com
forexcryptotrading[.]com
coinfxtrade[.]com
app[.]365coinoptions[.]com
www[.]fxbitcoinhub[.]com
coin24option[.]com
reliabletradeoptions[.]com
hugowayfx[.]com
tradebitcoinclubfx[.]com
bitforex24trading[.]com
fastcoinoption[.]com
365coinoptions[.]com
360liveoption[.]com
authorisedfxb[.]com
362tradesfx[.]com
44optionsfx[.]com
www[.]bit-primer[.]ltd
247paytrade[.]com
24forextradeoption[.]com
362liveoption[.]com
bit247options[.]com
forexoptionslive[.]com
fxbitcointrades[.]com
fxbrokerstm[.]com
fxstockstrades[.]com
stocknforex[.]com
cmcoptions[.]com
fxtradeunique[.]com
fxpaytrade[.]com
swifttrade247[.]com
unitedinvestmentcapital[.]com
tradexpremium[.]com
Operation N-Fiverr’s malicious wallet addresses:
12g2Dv756ayP7mmbXogaAE9EQeyyCUrSVR
152c4AfU5Q5Uh5SxVhjvMr85EBFT6XHzZy
15Kn9mUTzEwUen8zGgziazkPWwwyqTJNwC
15pQ83mfvLzs3E8uL17cZe7nDjfGN6NSKi
17CoLC6LVthEzyQC2oBX3mZxYLNPoz6ii6
18qWgXXttdN7QnrDy6XQhYTCobCwWBXjAw
19on4qXP4t6jf13gEfjgsPidQnvMdARKFh
1AmreEqxqaRowCdfcrqBmpxAvZwoqSaXAS
1AnFwUYT9UvkZZT2FoxTygyuP1PBfoyKW6
1AX2aXX6RWLzH6ZKFRHQXgjG8e3k5HyXpF
1BFPyMohqgdR4L6yibnoJqt3rxBK6xwakQ
1Bi2qvtibUCUSRGkWSRCnngV3hx3a6Fici
1BT5vBb9WKudUAX51jiWi3pAawobD3mZwM
1CdkyVQdh9w9WYMqbeiv9CWUXaoGmbUXEG
1DevmdaCCmuTfDw4FMdQwZzVe5pjTctE9j
1DTHCNVNaq6oGDXQXyPpspQoxDx8kRzdh1
1EfjgV217fDc9Kgt1PehmiV7TzistXEKX
1FjE7xCFNWpkxr6rH1j1GTrh38cUXezCkh
1FkCigBQiBzGZWWhJd9JwVjPFvYiVq6Zau
1FUG8fxsXtDGiFEg3RhfHqHPfMrV1yPNPc
1G7ViACQm5EqC21NYiWcSobGNvsg8Qgm99
1GTQiEaFSa6NMEffLbswzRD3o6PbYCBeD6
1HHinM5mbSeWNqADq822bYcirRNZmYw4Zp
1JG171jEfdo648Fvu8ekvLGUXUkdicazQC
1JKQnLm9xMN9pWiU9dYAjzhQa5swXk3wy8
1JyrkMsZNAToa94D9bqBR1WiC8g2orhiAW
1LaAgjZXcBJfXv1okEAXm4aCwENpSW1YFm
1LGuVkkUcxbyj5JtRo1TKyGEQV7LvhXnVF
1M5nPTDw8R8xAeXCy1P1ur6vVVRrBy1UcC
1P6noGHxYnouPPPFwE51YNB5qpadjNrMK6
1PnBSSZB2G2h96Mct7c1yQCtYksRJBRah3
1QH5V4n1XTJ4XvoPWTESwaotMgNQyk3Ma4
1RbgPxtnmQcVHdjuayYna5N6NTvbA9Yjd
32V1Jb9V42iXXip7jNYPzTwHAEha5PvxfY
34JzmxCYSFANjH5zdNYnYkc1YtcDzPzXNp
34PMa5tZgY4kMa7RiUTLGMrxkZvG1FkhVQ
35956a1Jwpx3XEaMYthBkWRibmxMoZ3owL
376SCgAAyy3om6c2v5dfZ5etYKwSC94D9C
37C28qoBx1D3ZdwjabgoCg525ZnWqwCRXV
39NiYSU4s73MFpxdHGqB365DYo3dFUFiD2
3BqSuVo11Xnq3k8qa3Kx6rv5im8zqz2dmU
3MvkG4qEz721b38SAk6kadzo99rBMYNDbh
3PjnVyDJqNYgh2kZ5YYzuWvVt3WuTr334a
1JAGYVTLbHYkAxyjfReFT8pjJABVYpnrDn
1N2ZPCeNJAtDRqE58nDNevRqdqV6w4uEgr
17HphcjnWLe3p4yv1bQX6mTqfpbgw8kBT1
1F52dWnX1AUwymHytYMN9XYXnAZgrhKhkA
1PzCz4fRMVUe5o3G8dqY63AG5Knaw2i3gF
13QdgoZ1uq5YMmVr14CHDbb9BDDxpwcK5e
15HhFZat5syJjSfZYefK1eutwYVWYyqy36
1AtgQRK2eDUtHakDApiynMfXrbNyaBjkVH
19dofMuyFRqDzC2HKh4bdUTht1Z6ojcGk5
13tauoqZ6ahtD7QSXkh7HcBr8HHb3v6sL5
16Suicij1cL4zjfftwiZ8PQpioKvjz5Qkb
14yfrcJDMxxFngAi9wfJ3X9Lqp6xEcFdwf
1EHdaQgGDVmXodh7oNdx4w1C4qiU4huVNm
1DKWmbfnhRHAo7XNc9UfsxsjzR98RzQ8cq
3BDPsuHKDFSjJAWGv4vEa72hmyT8knNJ3G
bc1qcpz9uu2mmsz4t8rrc9mswf9p8sprtknvxa33rh
0x0739fab47330C010ac1393E03D4e59691F286c16
0xad818dec93e9556f8c3c79b209733488496bf13c
0x0A8dA2C6Bd97134e73E7dC2f994A47Dcba21D368
0x9952d8a15db20a0e537a29096f5be448a6959e35
Operation N-Fiverr’s IP addresses
IP, Country, ASN
197[.]210[.]64[.]135, Nigeria, AS29465
197[.]210[.]28[.]149, Nigeria, AS29465
197[.]210[.]71[.]85, Nigeria, AS29465
197[.]210[.]54[.]202, Nigeria, AS29465
197[.]210[.]55[.]59, Nigeria, AS29465
197[.]210[.]226[.]133, Nigeria, AS29465
197[.]210[.]84[.]119, Nigeria, AS29465
197[.]210[.]54[.]162, Nigeria, AS29465
105[.]112[.]75[.]23, Nigeria, AS36873
105[.]112[.]97[.]190, Nigeria, AS36873
105[.]112[.]108[.]236, Nigeria, AS36873
105[.]112[.]101[.]160, Nigeria, AS36873
129[.]205[.]124[.]114, Nigeria, AS37148
Credits: Sun Huang, Wolf Chan, Wayne Huang, Yoyo Yu @ XREX
(Also published on Hacker Noon)