There’s plenty of buzz around Web 3.0 and innovations in blockchain and cryptocurrencies, but few understand the hidden risks of this technology.
As it is still emerging, widespread misuse raises concerns about fraud, money laundering, and hacking.
In this article, the XREX information security team will introduce information security in the Web3 world. We will learn simple to advanced security concepts, analyze hacking methods, and give you practical advice on protecting your personal information and digital assets.
What is Web 3.0 and why is it important?
Looking back at Web 3.0 predecessors, Web 1.0 and 2.0, will allow us to know why it is an important milestone.
- Web 1.0 & Web2.0
Since the 1990s, the internet has affected all aspects of our lives. From simple everyday tasks to politics, to economy, education, and communication, the list is long.
Over the past three decades, Web 1.0 and Web 2.0 have made the internet accessible to billions of people. Nonetheless, we also face significant challenges in adopting them.
Tech giants realized that personal information is a precious asset. They monopolized the internet industry and took control of user-generated data, information, and content.
People sacrificed security for the convenience of these services, whether or not they knew it. Once uploaded, personal information no longer belongs to the user but is centrally managed and utilized by a specific vendor.
For example, Facebook’s voice commenting system transcribes user voice files into text files for analysis by their AI systems. Google’s search algorithms collect user preferences and re-sale them to interested parties. Spotify exploits music creators and takes 30% of their profit. When online game operators stop their services, virtual items instantly become worthless.
Moreover, what we read on the internet may contain intentionally incomplete data and guided advertisements to influence our cognition and decision-making.
Although Web1.0 and Web2.0 introduced these problems, they also contributed to the birth of Web 3.0 or Web3.
- Web3
Web3 technology is considered the best solution for Web 1.0 and 2.0.
Web3 utilizes blockchain technologies with a decentralized structure, due to its immutability, openness, transparency, and open-source nature. It incentivizes users to take ownership and control their own data instead of relying on big tech companies.
In 2008, Satoshi Nakamoto published the Bitcoin white paper which introduced the concept of “decentralization.” This was a revolutionary concept. We immediately started to dream and began work on various DeFI projects, from Bitcoin, Ethereum, NFT, DeFi, and now the famous “Move-to-earn” app, STEPN.
Thanks to the implementation of different projects, users regained autonomy and freedom. Many DeFi projects implemented DAO (Decentralized Autonomous Organization) using blockchain so that users can share values and benefits through DAOs.
Yet as technology evolves, so do abuses. A common stereotype about cryptocurrencies is that it is usually associated with money laundering and fraud.
Blockchain is decentralized, which means users are responsible for protecting assets and identities. No institution or entity can alter or restore transactions on the blockchain. As a result, many criminal groups can execute scams and use DeFi vulnerabilities anonymously.
Damages/losses in Web3 security incidents
According to data from SlowMist, a well-known blockchain security company, from 2012 to June 2022, there were at least 787 hacking incidents in the entire blockchain ecosystem, with losses exceeding $26.7 billion.
According to The Federal Trade Commission (FTC), since 2021 more than 46,000 people have reported losing over $1 billion in crypto scams.
It is worth noting that this does not count global data and only records the data of reported cases, which means that many victims are still not on record. It is difficult for us to know the number of victims and the number of losses.
What do hackers want?
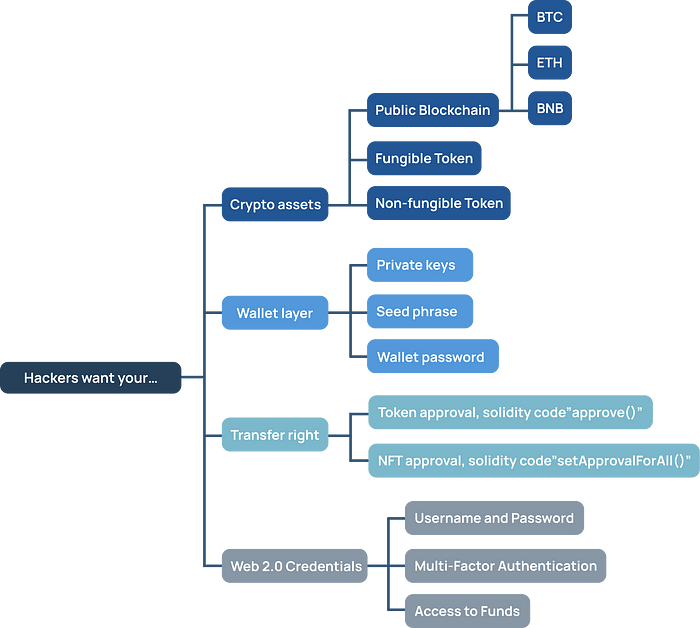
Based on the figure above, hackers can be classified into four categories based on their purpose:
- Crypto assets
- Wallet layer
- Transfer rights
- Web 2.0 credentials
To obtain illicit profits, hackers use various methods to get the following information:
- Use strong cryptocurrencies like Bitcoin and Ethereum, or high-priced NFTs, to obtain hard currency. The “give $1, and I will return $10” scheme is a classic investment gift scam.
- Find out private keys, tokens, or passwords of cryptocurrency wallets.
- Transfer the user’s virtual assets to another wallet after obtaining the user’s consent to transfer assets on a smart contract.
- Obtain the user’s account number and password in cryptocurrency exchanges from Web 2.0.
We know what hackers want; so what can we do to protect our data and assets? “You should always keep your friends close and your enemies closer.”
- Understanding common threats and attack methods can prevent one from being deceived and becoming a victim.
- Be alert at all times and keep up with modern information security awareness and habits.
- Lastly, before you confirm anything, question yourself if you have any doubts or uncertainty.
To help identify attacks and scams, XREX compiled nine Web3 attack methods. We will showcase three of them below.
Web3 attack methods — Part 1
1. Credential Phishing
Credential phishing starts with fake websites, such as phony exchange logins or airdrop unlock pages. Without being aware of these fake websites, a user may enter their real account information and passwords, resulting in stolen credentials.
Using tools such as Social-Engineer Toolkit (SET) and Goclone, hackers can copy the front-end design of a simple website directly to a local server and then register a domain name similar to the official website. Therefore, we should pay utmost attention to the authenticity of the URL.
In addition, fake communication messages can be a source of attack. These include email, social media, mobile text messages, phony customer service on Telegram, etc.
Credential phishing attacks are a low-cost and high-paying method for hackers because it costs only a few dollars to send 100,000 phishing messages. However, if just one or two people fall into these traps, the hack may be profitable, sometimes they even make extremely high illegal profits.
How to prevent credential phishing? XREX recommends:
Add frequently used websites to your Favorites or Bookmarks Bar to avoid phishing sites.
- Protect your passwords with a password manager like Lastpass, NordPass, or Keeper Security.
- Install anti–phishing plugins like Netcraft Extension, PeckShieldAlert, Scam Sniffer, Wallet Guard, or MetaShield in your browser to automatically detect phishing sites.
- Never use the same password for more than one account to prevent multiple accounts from being stolen by using one password.
- Set complex passwords. We recommend passwords have a minimum of 10 characters, including at least one uppercase letter, one lowercase letter, numbers, and one special symbol.
- If you find a suspicious website, please report it immediately. This is one way to protect the security of the DeFi ecosystem.
2. Ad-hijacking
Ad-hijacking (also known as brand poaching, direct linking, or URL jacking) is similar to credential phishing, except that ad-hijackers use a fake domain, copy the text of target brands’ ads, then use a higher cost-per-click (CPC).
Sometimes search-engine-optimization (SEO) ranks their site higher than official ones in search engine results. When a user searches by using a keyword, the first result may be a fake website, and thus unsuspecting users fall into a trap.
In the picture below, we queried STEPN, the recently popular “Move-to-earn” app, as an example. Search STEPN on Google, and the top four results are all fake sites.
How to prevent ad-hijacking? XREX recommends:
- Pay extra attention to suspicious domains when searching for keyword clicks.
- Add frequently used websites to Your Favorites or Bookmarks Bar to avoid phishing sites.
- Install anti–phishing plugins like Netcraft Extension, PeckShieldAlert, Scam Sniffer, Wallet Guard, or MetaShield in your browser to automatically detect phishing sites.
- If you find a suspicious website, please report it immediately.
3. Fake customer service
Hackers pretend to be official employees of DeFi projects on social media. They trick users into filling out forms such as airdrop registration and service satisfaction surveys.
If a user takes the bait, the hacker will ask further questions to get a victim’s wallet address and personal information or transfer virtual currency to the hacker’s wallet address.
For example:
“The threshold for real-name verification does not match, and the wallet address needs to be verified.”
“Need to transfer cryptocurrency to a specified wallet address to unlock the password.”
How to avoid fake customer service scams? XREX recommends:
- Don’t trust unsolicited private messages from Telegram or other social platforms. Official projects will never suddenly send personal messages to users and ask for account information.
- If you have concerns about divulging sensitive information, such as deposit and withdrawal, real-name authentication, or account security, please contact the official website channel for assistance.
- Strengthen the privacy settings on Telegram. Set “Only my contacts can add me.” Please refer to the following steps to complete the settings:
At this point, we have discussed the definition of Web3, damages/losses in Web3 security incidents, the intentions and goals of hackers, and three attack methods with prevention recommendations.
In the next article, we will continue to analyze more Web3 attacks and scams.
Read Part 2 here.
Co-editors:Sun Huang / Wolf Chan / Seal Cao / Yoyo Yu / Helen Lai / Simon Liu