Author / Sun Huang, Chief Security Officer at XREX Inc.
As the Chief Security Officer of XREX, I started blockchain Web3 security internal training in March to improve our know-how in Web3 security analytical skills, and also blockchain and cryptocurrency anti-money laundering (AML) threat analysis.
We started by hosting a few internal Web3 and security workshops. Through the experience of improving the engineering team’s knowledge using real case studies, I compiled these two open-source repositories DeFiHackLabs and DeFiVulnLabs as learning material and for information sharing.
Every time a DeFi project is hacked, XREX internally analyzes the root cause of the incident and attempts to reproduce the hacker’s methodology. We simulate the method of the perpetrator’s attack vector on smart contracts by using a fork of a specific block from the mainnet, then observe changes in the balance status. Every attack incident is a lesson to help us avoid making the same mistakes for our future development.
I believe these valuable experiences can also benefit more people. So in mid-June, a Web3 security tool, DeFiHackLabs, was open-sourced and the Proof of Concept (POC) of past analyzed security incidents is now available to anyone.
I used Foundry, an Ethereum development tool launched by Paradigm, as the framework because it is fast to compile, integrates many practical functions and is easy to use. For more information on Foundry, please refer to the Foundry Book.
My original intention was to contribute to information security as Web3 is still developing. I published my work on Twitter as I would do normally. To my surprise, I received numerous Twitter notifications soon after tweeting and found that my tweet was retweeted by Georgios Konstantopoulos, CTO of Paradigm, drawing a good response from the community.
Afterward, I received many private messages, asking if there is any tutorial on common vulnerabilities in Solidity suitable for newbies or new engineers.
Upon learning about these needs, I developed another open-source tool, DeFiVulnLabs, in early July. It includes a curated list of common Solidity vulnerability testing and defense methods. I was surprised by the number of retweets and traffic of 40,000 visits in a single day. It can only be concluded that many people are interested in blockchain technology development and actively want to improve their information security capabilities.
I am excited about how this has turned out, and I look forward to continuing my work on Web3 in the future and contributing to our collective knowledge.
In this blog, I’m sharing with you DeFiHackLabs and DeFiVulnLabs, two sets of Web3 security tools, and how to use them. I hope that these tools will aid you when you build smart contracts and develop DeFi projects. Hopefully, you will be able to avoid falling into some common and advanced pit-falls.
DeFiVulnLabs (Level: Beginner)
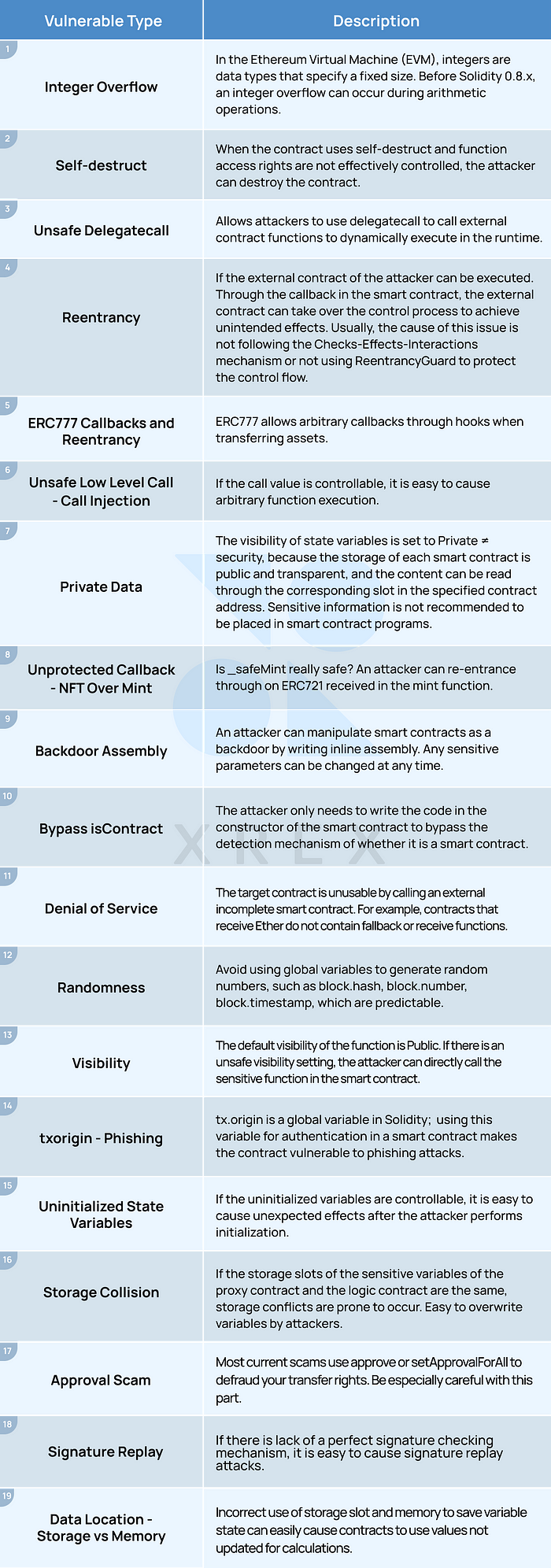
DeFiVulnLabs currently includes 19 common types of vulnerabilities in smart contracts, as listed in the following table:
How to use:
Take ERC777 callbacks and reentrancy as an example:
The smart contract requires that the total supply of tokens must be ≤ 1000. Otherwise, new tokens are not allowed to be minted. Can you bypass the maximum total supply limit?
Execute: forge test––contracts ./src/test/ERC777-reentrancy.sol -vvv
The -v parameter represents logs and Execution traces of the test code with a total of five levels.
The execution output looks like this:
We excerpted key execution traces to explain why the token balance can be increased from 1,000 to 10,000, as shown in the following figure:
It can be seen that when the attack contract ContractTestcalls MyERC777.transfer(), the ERC1820Registry contract will call back ContractTest.tokensReceived(), which means that the attacker can write malicious code in tokensReceived() and re-enter the execution flow of the MyERC777contract again.
The malicious code here is to call MyERC777.mint() again, causing the token contract to mint 9,000 tokens to the attacking contract again. Finally, you can see that the balance of the attack contract has a total of 10,000 Tokens.
DeFiHackLabs(Level: Intermediate)
DeFiHackLabs currently includes 46 reproductions of past DeFi security incidents. You can learn past attack methods from the real world and avoid stepping into the same pit!
Recently, Foundry supports the ability to fork different blocks at one time, or cross-chain, without bringing in the fork-url from the CLI and fork-block-number parameter is more convenient for testing.
How to use:
Take InverseFinance — Flashloan and Price Oracle Manipulation as an example:
Execute: forge test––contracts ./src/test/InverseFinance_exp.sol -vvv
Co-editors:Sun Huang / Seal Cao /Simon Liu /尤芷薇 / Fred Lai
The Chinese version of this article XREX 資安長開源兩套 Web3 資安工具 強化智能合約安全開發 is published on 29 July 2020 on the XREX blog.